What version of NoICE are you using? The latest is 9.8, which includes a monitor specifically for the 8080. It doesn't have many differences from the 8085 version, but there are some difficulties with the 8080 if your program enables interrupts (see the tail of my response below). So you may want to compare Mon8080.asm (attached for your convenience) with your monitor.
For the 8080 and other targets using the serial protocol, NoICE does single-step by automatically setting and removing breakpoints.
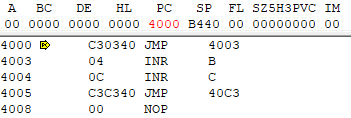
Mon8080.asm as provided in the 9.8 install uses RST 1 for breakpoints. So in your example, when you press F7 NoICE should replace the INR B with an RST 1, and then tell the program to execute.
When the 8085 executes the RST 1, it should push PC, which will point at the instruction after the RST 1, or 4004.
The monitors' handler for RST 1 pushes PSW (two bytes, A and flags), loads A with 1, and jumps to INT_ENTRY
INT_ENTRY stores A as REG_STATE, does some other register storing, then
Code: Select all
; If entry here was by breakpoint (state=1), then back up the program
; counter to point at the breakpoint/RST instruction. Else leave PC alone.
; (If CALL is used for breakpoint, then back up by 3 bytes)
POP H ;GET PC OF BREAKPOINT/INTERRUPT
LDA REG_STATE
DCR A
JNZ NOTBP ;JIF NOT A BREAKPOINT
DCX H ;BACK UP PC TO POINT AT BREAKPOINT
NOTBP: JMP ENTER_MON ;HL POINTS AT BREAKPOINT OPCODE
So the pushed PC of 4004 SHOULD get decremented to 4003 before the jump to ENTER_MON.
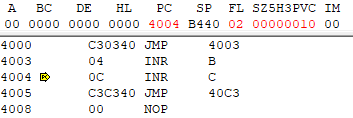
ENTER_MON reports the stop and current registers to NoICE, which then puts back the INR B op-code and shows the registers.
It is interesting that in your screen shots, B is NOT incremented. And by perverse coincidence, the low byte of the jump address happens to be the op-code for JMP.
Please try this: with PC at 4000 as shown in your first screenshot, select "Options", "Show Communications"
Then press F7. A spy window should appear showing the bytes set to and received from the target.
When the target stops, presumably looking like your second screenshot, right-click in the spy window, click "select all", then right-click and "copy". Paste the results into email so that I can see what the target is reporting. (If you are interested, you can decode the bytes yourself by referring to the protocol description at https://www.noicedebugger.com/help/work ... sicMonitor)
Were 8080 interrupts enabled during your test? One hassle with the 8080 is that there is no simple way to TELL whether or not interrupts are enabled. On many processors, such as HC11, there is an interrupt-enable bit in the processor status word that can be checked. The 8085 has the RIM instruction, which allows interrupt enable state to be read.
But on the 8080, there is nothing built in. There IS a hardware pin showing state, but you would need to provide hardware to read it, and code in Mon8080.asm to use the hardware. See more on this at
https://www.noicedebugger.com/help/targets.htm#8085
Best regards, John Hartman